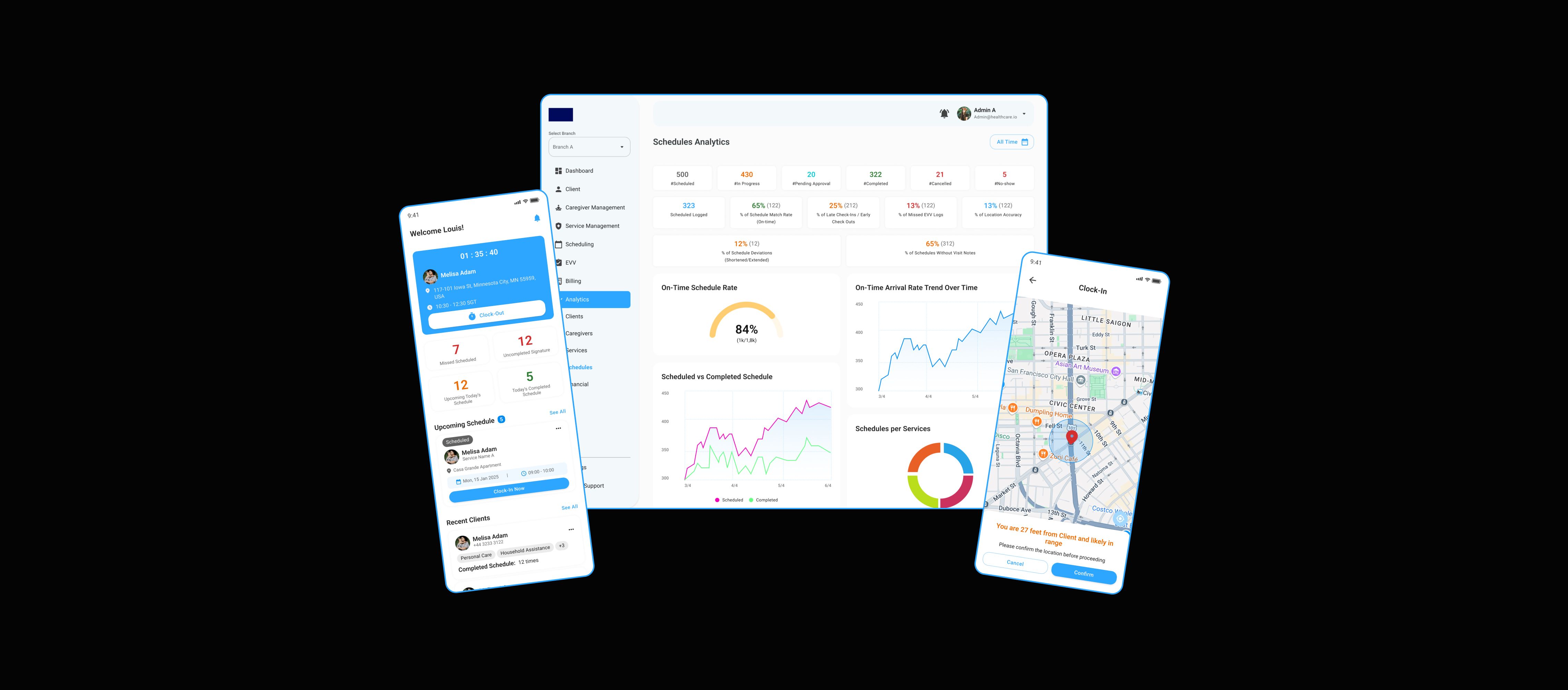
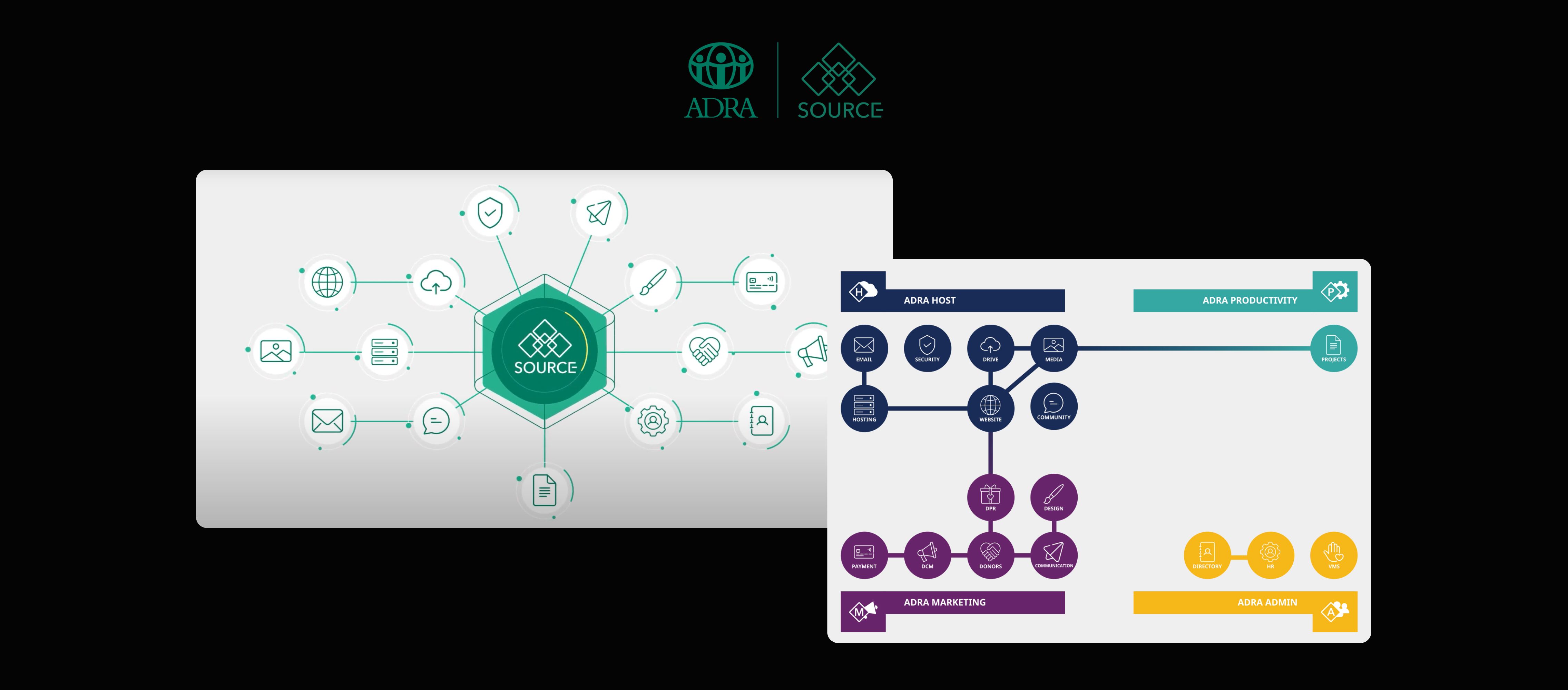
Ready to Invest in a Digital Solution That Lasts?

Contact Us
Get in Touch with Blue Horn Tech
Reach out today, and let’s discuss how we can empower your business with secure, customized solutions.
Get answers to common questions.
Have a quick question? Check out our FAQs for instant answers.
What services does Blue Horn Tech offer? arrow_drop_down
Can I schedule a consultation? arrow_drop_down
Do you work with clients outside the United States? arrow_drop_down
What sets Blue Horn Tech apart from other tech solution providers? arrow_drop_down
What’s the cost structure for your services? arrow_drop_down
What’s the typical timeline for a project? arrow_drop_down
What industries does Bue Horn Tech specialize in? arrow_drop_down
How soon will I receive a response? arrow_drop_down
What is the process for starting a project with Blue Horn Tech? arrow_drop_down


fg?q=80)