Your Partner in Identity Access and Secure Web Development
Unlock the full potential of your digital landscape with our secure Identity Access and Web Development services, tailored for modern business needs
Solutions for a Secure and Connected Future
From enterprise security to seamless user access, we’ve got the solutions your business needs.
Identity and Access Management (IAM)
Empower your organization with innovative identity management solutions designed to secure access and streamline operations.
Keycloak Implementation and Customization
Identity Federation and Single Sign-On (SSO)
Migration to Keycloak
Custom IAM Development
Security Audits and Compliance
Training & Support Services
Software Development
Secure, scalable software tailored to your business goals—from web platforms to mobile apps and automation systems.
Mobile Application Development
Role-based Access Control (RBAC)
Custom Web Development
Security-Focused Architecture
UI/UX Design

System Integration Services
Unify your tools and automate your operations with integration solutions built for speed, accuracy, and growth.
API Integration & Middleware Solutions
Enterprise System Integration
Legacy System Modernization
Data Synchronization & Workflow Automation
Proven Impact, Trusted Solutions
Real numbers that show how we’re making digital security and development better for our clients.

10+
Years of Experience
5+
Industries Served
10+
Successful Project
99%
Uptime and Reability
Our Work in Action
Explore our portfolio to see how we’ve transformed businesses across industries with secure, innovative digital solutions.

MyCoachingTree
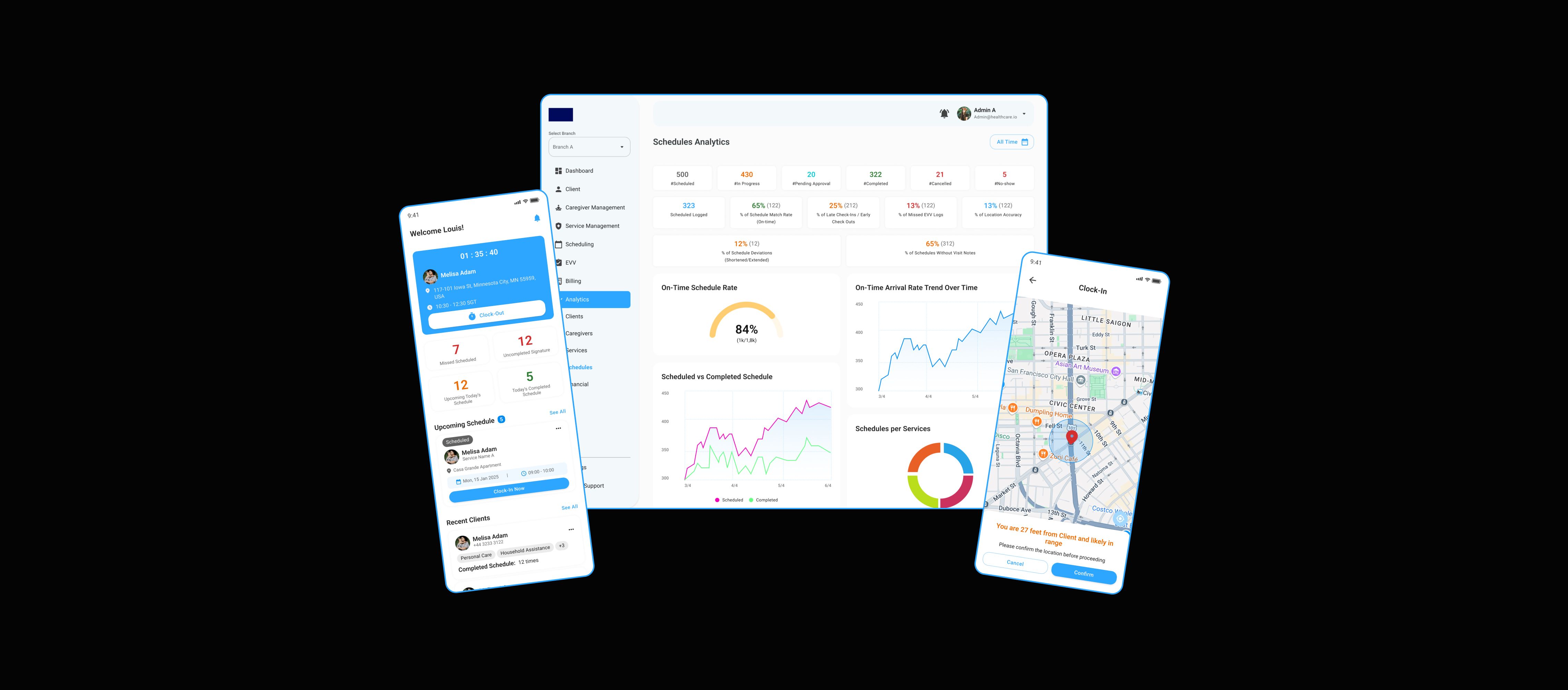
Blue Horn Tech developed a centralized SSO authentication system for MyCoachingTree’s platforms, integrating SmartJobBoard and MightyNetworks with Keycloak.
MyCoachingTree
Blue Horn Tech developed a centralized SSO authentication system for MyCoachingTree’s platforms, integrating SmartJobBoard and MightyNetworks with Keycloak.
2025
. . . . . . . . . . . .
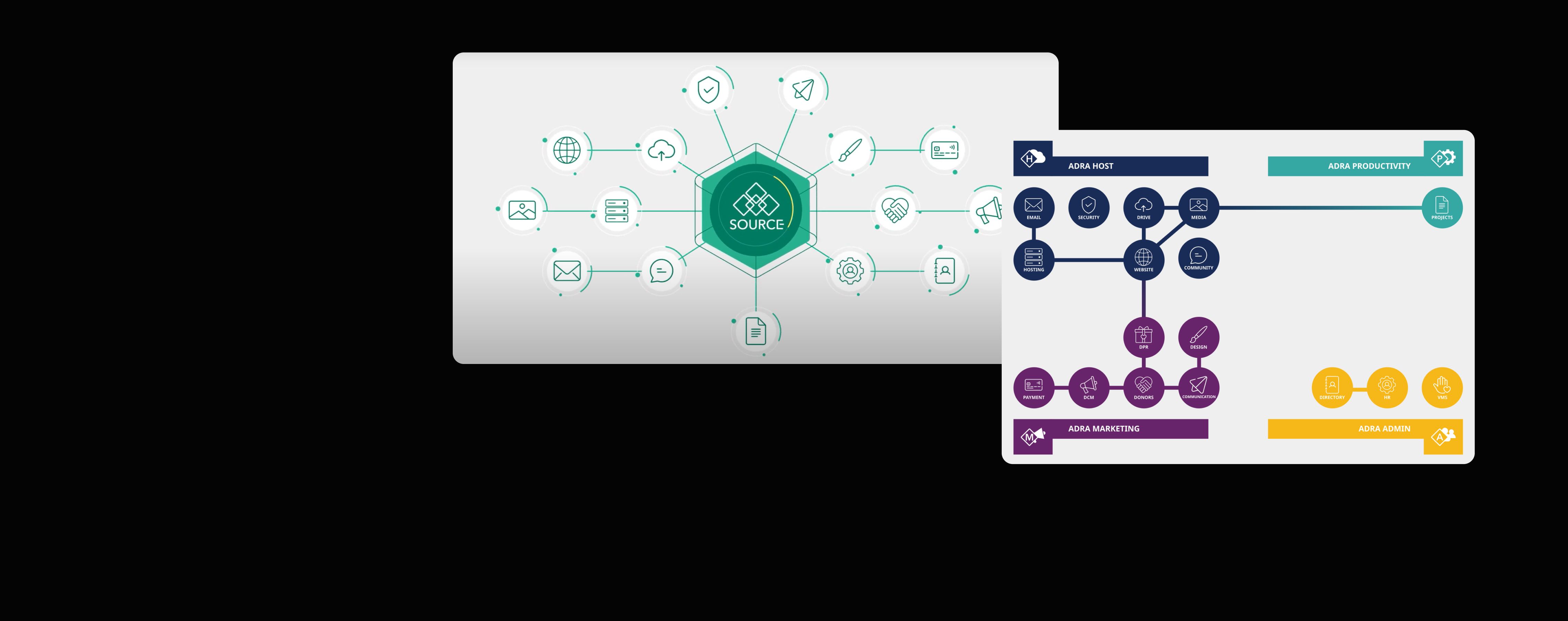

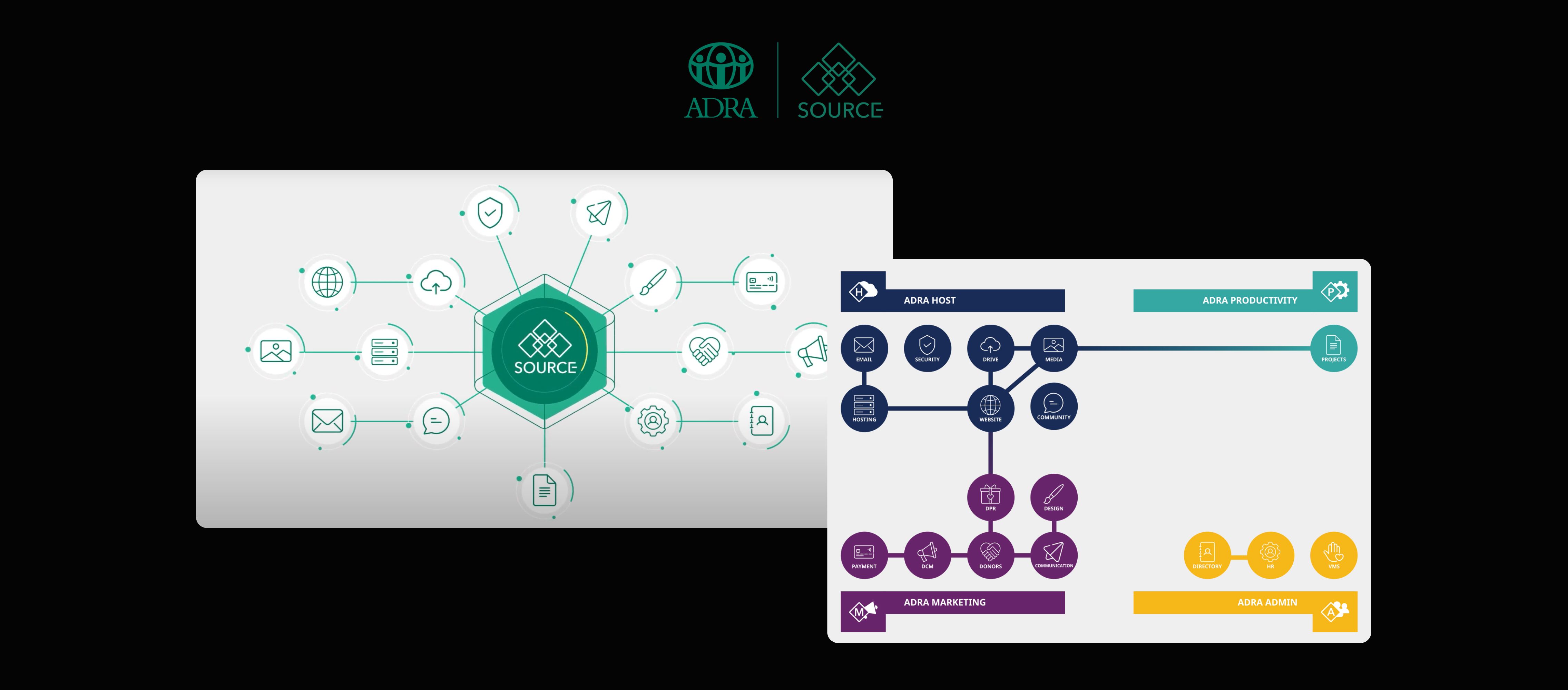
ADRA
Reduced login friction and boosted efficiency for ADRA by integrating critical platforms and enabling secure Single Sign-On using Keycloak.
ADRA
Reduced login friction and boosted efficiency for ADRA by integrating critical platforms and enabling secure Single Sign-On using Keycloak.
2025
. . . . . . . . . . . .
Why Choose Blue Horn Tech?
You’re getting more than just a solution. You’re getting a dedicated team, a security-first mindset, and a long-term partner committed to your success.
Security-Focused
Our solutions prioritize security, ensuring your data and operations are protected at all levels.
!EKZg?q=80)
Client-Centric
Every solution we deliver is crafted with your business’s unique needs in mind.
Innovation-Driven
Using the latest technologies, we provide secure, scalable solutions that evolve with you.

Compliance-Ready
Our solutions meet industry standards, keeping you secure and compliant.
Hear From Our Satisfied Clients
Our clients aren’t just projects—they’re partners. Here’s what they have to say about our work and how we’ve helped them reach their goals.
Insights from Our Experience
Explore our latest insights to stay informed on the trends, best practices, and innovations in Identity Access Management and Web Development.
Ready to Invest in a Digital Solution That Lasts?
We’re experts in creating solutions that drive growth, secure data, and engage users. Start your journey with us today.
fg?q=80)